Background Verification
Tailored Solutions For Your Security Priorities
Background Verification Services (BVS) involves a comprehensive, ethical
investigation into an individual’s history. This service typically covers criminal records,
academic qualifications, employment history, and professional references
For a business, BVS is a vital risk management tool. By rigorously
validating the claims and history of prospective employees or partners, we protect your
organization from liability associated with negligent hiring, fraud, and potential intellectual
property theft. Our process is meticulously tailored to navigate the complex landscape of
regional data access, ensuring that the reports provided are accurate, actionable, and
adhere to strict privacy standards.
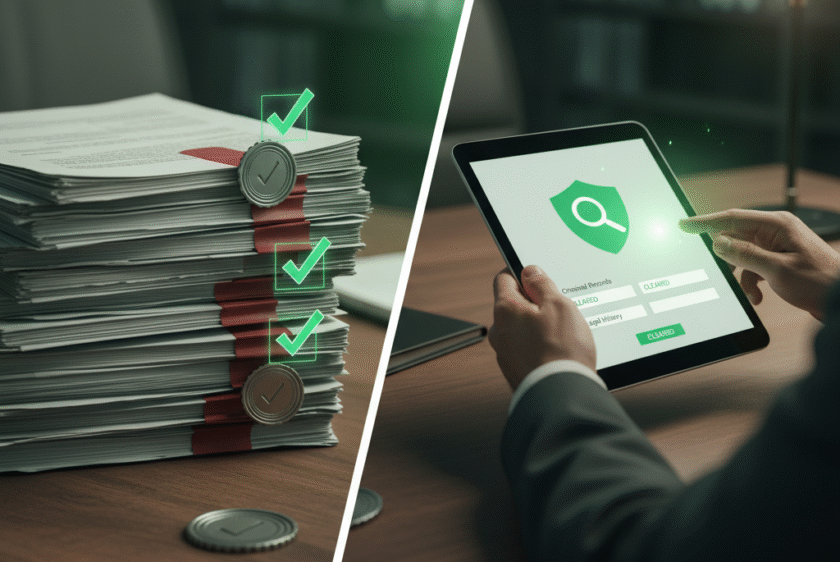
This service is absolutely critical for the digital economy, acting as the
first line of defense against synthetic identity fraud, impersonation, and account takeover.
Authenticate Cyber Security provides seamless, API-driven verification workflows that
allow businesses to comply with Know Your Customer (KYC) and Anti-Money Laundering
(AML) regulations while improving customer onboarding speed. Our IVS essentially
transforms anonymous digital interactions into authenticated, trustworthy business
relationships.
Key Benifits
Reduces Financial Exposure: By identifying applicants with histories of financial fraud, theft, or unethical conduct, BVS directly prevents potential financial losses for the company.
Prevents Negligent Hiring Claims: Verifying a candidate's background demonstrates due diligence, protecting your organization from legal liabilities if an employee harms another individual or commits a crime in the workplace.
Criminal Records: Checks for legal history where accessible.
Educational Credentials: Directly verifying degrees and certifications with issuing institutions.
Previous Employment: Confirming job titles, tenure, and reasons for departure.
Identity Validation: Ensuring the person is who they claim to be using official documents.
Our local expertise ensures the verification process is compliant, accurate, and effective, navigating regional data challenges.
Informed Consent: We require clear, written consent from the candidate before initiating any verification checks.
Data Minimization: We only collect and process data that is absolutely necessary for the verification purpose.
Secure Handling: All sensitive information is handled and stored using secure, encrypted protocols, ensuring confidentiality throughout the process.
Authenticated pathways for emergency vehicles to override signal timings

Anomaly Detection & Attack Surface Monitoring

We Take Care Of Everything For You
Secure Integration of AI Analytics
AI cameras are used for traffic counting, incident detection, or
predictive modeling, we ensure the processing environment is isolated and the analytical outputs are
verified as tamper-proof before being used to adjust live traffic settings
Keep An Eye On Everything With Our Video Security!
Request A Quote
Quick Contact
18 Biambo Street Amadi ama Port Harcourt, Rivers State Nigeria.

