Corporate Digital Security
Tailored Solutions For Your Security Priorities
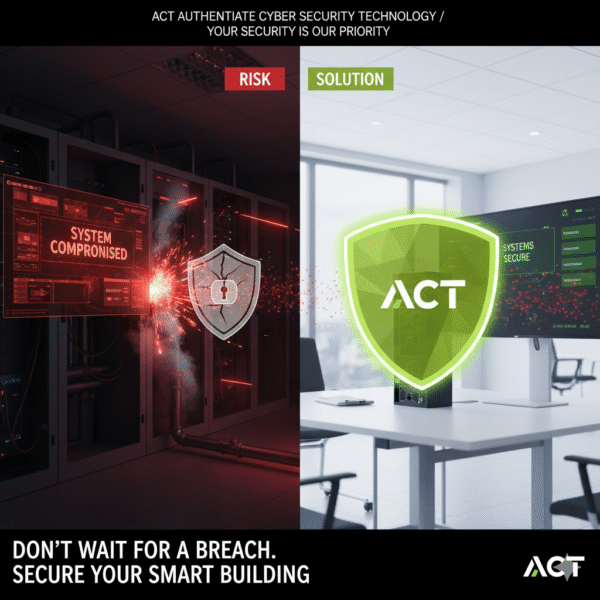
Authenticate Cybersecurity specializes in securing this convergence point. We ensure that every
credential check, every vehicle scan, and every access command is authenticated, encrypted, and audit-ready.Our solutions enforce a principle of Zero-Trust at the perimeter, verifying every user and device trying to
gain entry.
We protect the communication between access readers
(card/biometric/mobile) and the central Access Control System (ACS). All identity data transmission is
encrypted and securely tokenized, minimizing the risk of credential theft or spoofing.
LPR Anti-Spoofing & Integrity: Our systems utilize advanced authentication protocols for LPR cameras,
ensuring the vehicle image and plate data are verified as authentic, preventing hackers from using
digital manipulation (like replayed images) to gain access.

Corporate Digital Security (CDS) involves strategic consulting and
implementation focused on achieving enterprise-wide digital resilience. This service
integrates technology with policy, governance, risk, and compliance (GRC) frameworks.
CDS is about making security a business enabler, not just an IT task. Our
consultants work directly with executive leadership to develop tailored security
architecture, craft robust Incident Response Plans (IRPs), and implement organizational
policies based on principles like Zero Trust. This systematic approach ensures that security
investments are aligned with strategic business objectives and meet all necessary
regulatory mandates.
Key Benifits
CDS goes beyond basic defense to integrate security into the very fabric of your business strategy, ensuring resilience and sustainable growth.
Strategic Risk Alignment and Governance
Translates Security into Business Value: CDS ensures security investments are strategically aligned with corporate objectives, protecting critical revenue streams and intellectual property, rather than simply being a cost center.
Achieves Regulatory Compliance (GRC): We establish frameworks (Governance, Risk, and Compliance) that help your company meet stringent local and international data protection laws, avoiding massive fines and legal liabilities.
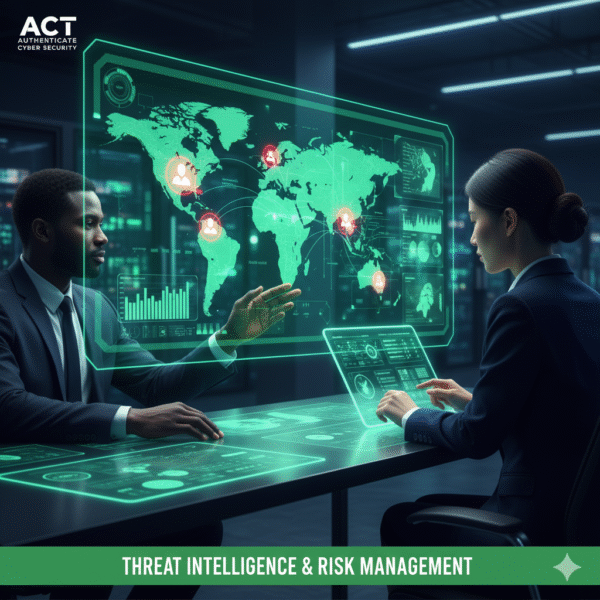
Enables Informed Decision Making: Provides executive leadership with clear, non-technical risk reports and dashboards, allowing for data-driven strategic decisions regarding security posture.
Data Mapping: Identifying where sensitive data resides.
Control Implementation: Applying technical and policy controls (e.g., encryption, access restrictions) required by frameworks like GDPR or local data protection acts.
Keep An Eye On Everything With Our Video Security!
Request A Quote
Quick Contact
18 Biambo Street Amadi ama Port Harcourt, Rivers State Nigeria.

